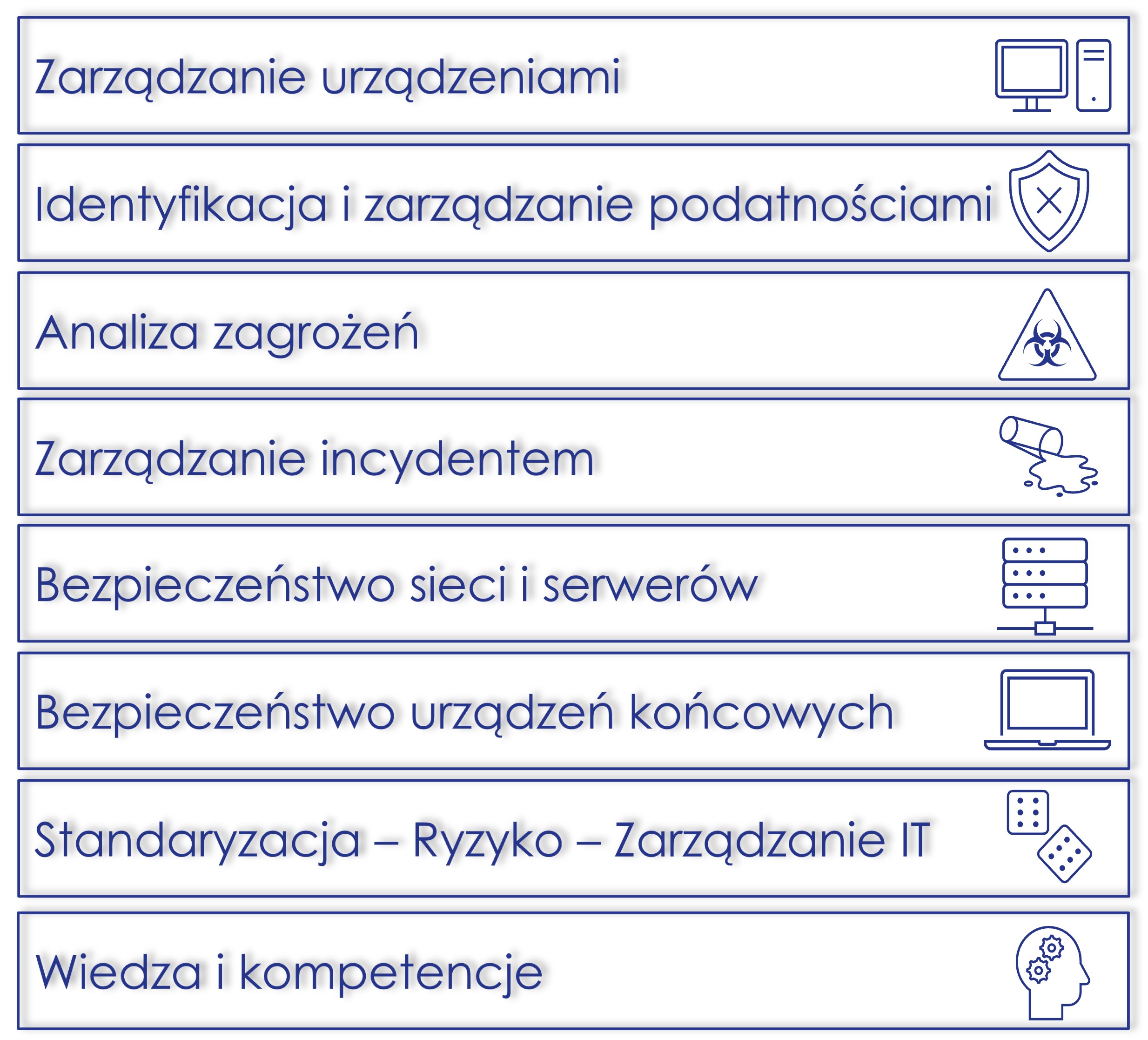
 cyber security
cyber security
Managed Security Services (MSS)
Cybersecurity, data and systems security require more and more investments, skills, knowledge and commitment of the organization. This is the result of an increasing number of and sophisticated attacks, but also of an increasing amount of data, a lack of employee awareness and increasing legal requirements in the field of security.
Blue Energy on a 24/7 basis, 365 days a year, can ensure your safety. Use our services and we will ensure comprehensive security of your organization.
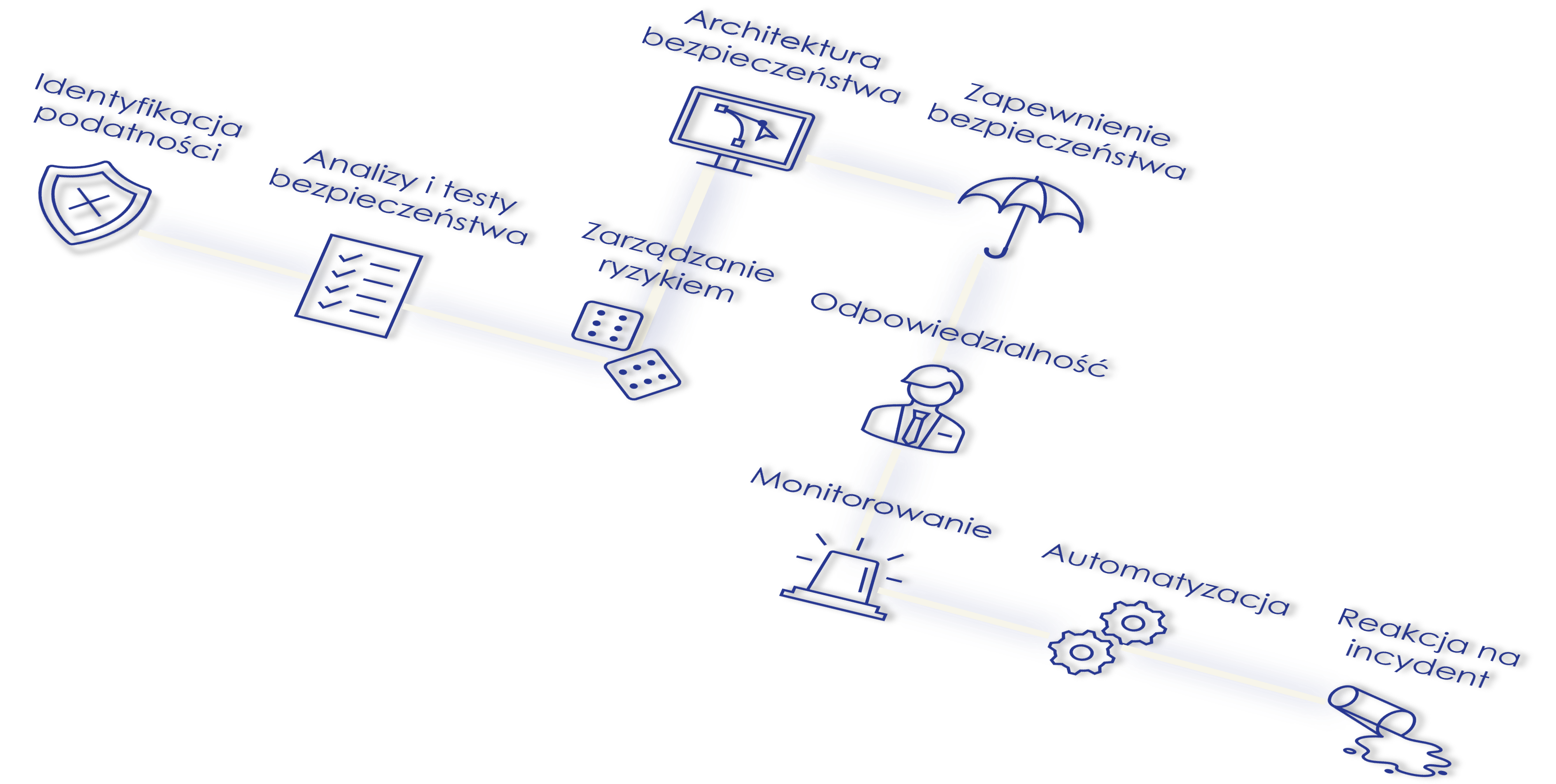
Our services range from prevention, identification of vulnerabilities and threats, tuning of security mechanisms, building a security architecture, to incident response.

Vulnerability identification
Our consultants use dedicated tools to analyze vulnerabilities – weaknesses of your resources, IT systems and security. You can read more about vulnerability analysis in the article
Security analysis and testing
We conduct security tests aimed at exploiting vulnerabilities and breaking security – more
We perform security analyzes, including analyzes related to user awareness research – social engineering analyzes and tests aimed at researching and raising awareness by performing sham attacks.
Risk management
We automate risk analysis based on the importance of the systems and processes they support. We prioritize actions and select safeguards depending on the level of effects. We plan activities and security areas based on risk levels. We visualize the results of analyzes and automate activities.
& nbsp;
Security Architecture
We design a security system based on the results of the risk analysis and legal analysis assessment. We apply international safety standards that ensure comprehensive and universal solutions.
To ensure security
We remove vulnerabilities, implement security measures that immunize to threats, and conduct awareness campaigns.
Responsibility

Comprehensive
Our professional-designed service delivery processes and innovative tools allow us to provide comprehensive, comprehensive services. We respond to all the needs of our clients, both the smallest ones related to the monitoring of a selected part of the infrastructure, to the most complex ones.
Professionally
Our experts provide the highest level of service thanks to the highest level of competence, service customization and excellent tools. Details about us….
Cheap
We provide the best cybersecurity experts, engineers, lawyers, social engineers and top-class tools to help ensure cybersecurity at an affordable price in the subscription model.
Comprehensive, professional and cheap, is it possible?
It is estimated that cybercrime will bring up to 5 times more profits than global international crime combined. Who can afford to repel such a massive attack? The increase in digitization of business and everyday life means that the number of cybersecurity challenges is growing exponentially.
Growing legal requirements in the scope of ensuring the security of processed data, e.g. personal data, may also cause problems.
Providing such broad competences requires considerable expenditure and requires constant development, which is also not simple and cheap.
Comprehensive
Our professional-designed service delivery processes and innovative tools allow us to provide comprehensive, comprehensive services. We respond to all the needs of our clients, both the smallest ones related to the monitoring of a selected part of the infrastructure, up to the most complex.
Professionally
Our experts provide the highest level of service thanks to the highest level of competence, service customization and excellent tools. Details about us….
Cheap
We provide the best cybersecurity experts, engineers, lawyers, social engineers and top-class tools to help ensure cybersecurity at an affordable price in the subscription model.
Comprehensive, professional and cheap, is it possible?
It is estimated that cybercrime will bring up to 5 times more profits than global international crime combined. Who can afford to repel such a massive attack? The increase in the digitization of business and everyday life is making the number of cybersecurity challenges grow exponentially.
Growing legal requirements in the scope of ensuring the security of processed data, e.g. personal data, may also cause problems.
Providing such broad competences requires considerable expenditure and requires constant development, which is also not simple and cheap.


Articles
Ile faktycznie zajmuje identyfikacja i realizacja praw podmiotu danych? Czy nasz rejestr czynności wspiera realizację praw? Czy potrafimy automatyzować procesy realizacji praw podmiotu danych?

Krajowy System Cyberbezpieczeństwa to wymagania dla operatorów usług kluczowych oraz usług cyfrowych. Czym są te wymagania opisane w dość oszczędny sposób w Ustawie? Co mówi sama ustawa o tym jak zapewnić bezpieczeństwo i ciągłość realizacji usług kluczowych?

Częstym problemem organizacji jest zapewnienie efektywnego i gwarantującego właściwą rozliczalność kanału komunikacji wewnętrznej, np. związanej z realizacją praw podmiotów danych, czy zgłaszaniem i obsługą naruszeń ochrony danych osobowych








